2018 Exam PCNSE7 Dumps From Lead2pass Cover All New PCNSE7 New Questions.v.2018-1-10.226q
https://www.lead2pass.com/pcnse7.html
QUESTION 147
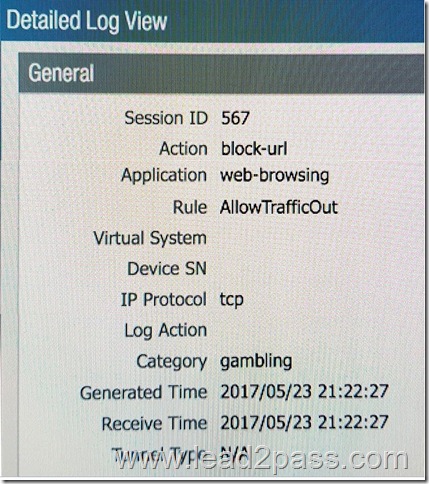
Refer to exhibit. An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms. The network team has reported excessive traffic on the corporate WAN.
How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all existing monitoring platforms?
A. Forward logs from firewalls only to Panorama and have Panorama forward logs to other external services.
B. Forward logs from external sources to Panorama for correlation, and from Panorama send them to the NGFW.
C. Configure log compression and optimization features on all remote firewalls.
D. Any configuration on an M-500 would address the insufficient bandwidth concerns.
Answer: C
QUESTION 148
Which Captive Portal mode must be configured to support MFA authentication?
A. NTLM
B. Redirect
C. Single Sign-On
D. Transparent
Answer: B
QUESTION 149
Which protection feature is available only in a Zone Protection Profile?
A. SYN Flood Protection using SYN Flood Cookies
B. ICMP Flood Protection
C. Port Scan Protection
D. UDP Flood Protections
Answer: A
QUESTION 150
Which User-ID method maps IP addresses to usernames for users connecting through an
802.1x-enabled wireless network device that has no native integration with PAN-OS?software?
A. XML API
B. Port Mapping
C. Client Probing
D. Server Monitoring
Answer: A
Explanation:
Captive Portal and the other standard user mapping methods might not work for certain types of user access. For example, the standard methods cannot add mappings of users connecting from a third-party VPN solution or users connecting to a 802.1x-enabled wireless network. For such cases, you can use the PAN-OS XML API to capture login events and send them to the PAN-OS integrated User-ID agent
QUESTION 151
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
A. Configure the option for “Threshold”.
B. Disable automatic updates during weekdays.
C. Automatically “download only” and then install Applications and Threats later, after the administrator approves the update.
D. Automatically “download and install” but with the “disable new applications” option used.
Answer: C
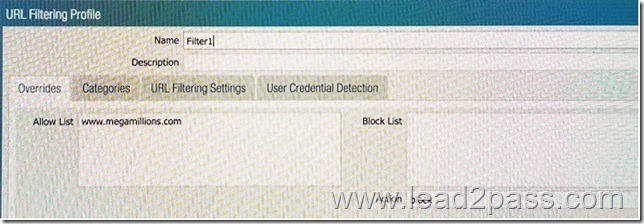
QUESTION 152
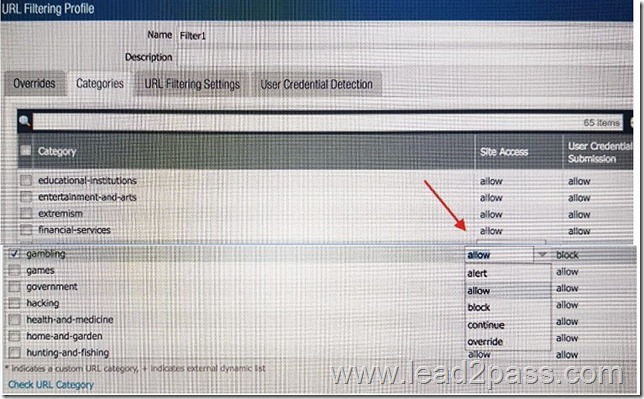
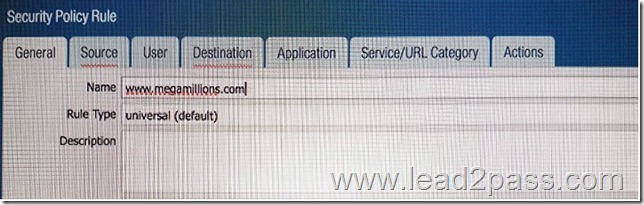
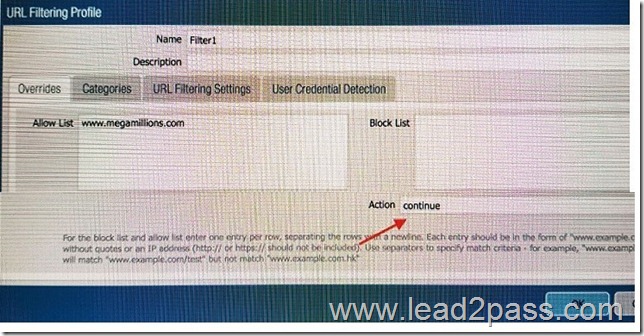
An administrator needs to determine why users on the trust zone cannot reach certain websites. The only information available is shown on the following image. Which configuration change should the administrator make?
Answer: B
QUESTION 153
An administrator has users accessing network resources through Citrix XenApp 7 x. Which User-ID mapping solution will map multiple users who are using Citrix to connect to the network and access resources?
A. Client Probing
B. Terminal Services agent
C. GlobalProtect
D. Syslog Monitoring
Answer: C
QUESTION 154
An administrator creates a custom application containing Layer 7 signatures. The latest application and threat dynamic update is downloaded to the same NGFW. The update contains an application that matches the same traffic signatures as the custom application.
Which application should be used to identify traffic traversing the NGFW?
A. Custom application
B. System logs show an application error and neither signature is used.
C. Downloaded application
D. Custom and downloaded application signature files are merged and both are used
Answer: A
QUESTION 155
How can a candidate or running configuration be copied to a host external from Panorama?
A. Commit a running configuration.
B. Save a configuration snapshot.
C. Save a candidate configuration.
D. Export a named configuration snapshot.
Answer: D
QUESTION 156
A company needs to preconfigure firewalls to be sent to remote sites with the least amount of reconfiguration. Once deployed, each firewall must establish secure tunnels back to multiple regional data centers to include the future regional data centers.
Which VPN configuration would adapt to changes when deployed to the future site?
A. Preconfigured GlobalProtect satellite
B. Preconfigured GlobalProtect client
C. Preconfigured PIsec tunnels
D. Preconfigured PPTP Tunnels
Answer: A
QUESTION 157
A global corporate office has a large-scale network with only one User-ID agent, which creates a bottleneck near the User-ID agent server. Which solution in PAN-OS?software would help in this case?
A. Application override
B. Redistribution of user mappings
C. Virtual Wire mode
D. Content inspection
Answer: B
QUESTION 158
Which CLI command is used to simulate traffic going through the firewall and determine which Security policy rule, NAT translation, static route, or PBF rule will be triggered by the traffic?
A. check
B. find
C. test
D. sim
Answer: C
QUESTION 159
If the firewall is configured for credential phishing prevention using the “Domain Credential Filter” method, which login will be detected as credential theft?
A. Mapping to the IP address of the logged-in user.
B. First four letters of the username matching any valid corporate username.
C. Using the same user’s corporate username and password.
D. Marching any valid corporate username.
Answer: A
QUESTION 160
Which Security policy rule will allow an admin to block facebook chat but allow Facebook in general?
A. Deny application facebook-chat before allowing application facebook
B. Deny application facebook on top
C. Allow application facebook on top
D. Allow application facebook before denying application facebook-chat
Answer: A
QUESTION 161
Which feature prevents the submission of corporate login information into website forms?
A. Data filtering
B. User-ID
C. File blocking
D. Credential phishing prevention
Answer: D
QUESTION 162
Which three steps will reduce the CPU utilization on the management plane? (Choose three.)
A. Disable SNMP on the management interface.
B. Application override of SSL application.
C. Disable logging at session start in Security policies.
D. Disable predefined reports.
E. Reduce the traffic being decrypted by the firewall.
Answer: CDE
QUESTION 163
Which two virtualization platforms officially support the deployment of Palo Alto Networks VM-Series firewalls? (Choose two.)
A. Red Hat Enterprise Virtualization (RHEV)
B. Kernel Virtualization Module (KVM)
C. Boot Strap Virtualization Module (BSVM)
D. Microsoft Hyper-V
Answer: BD
QUESTION 164
To connect the Palo Alto Networks firewall to AutoFocus, which setting must be enabled?
A. Device>Setup>Services>AutoFocus
B. Device> Setup>Management >AutoFocus
C. AutoFocus is enabled by default on the Palo Alto Networks NGFW
D. Device>Setup>WildFire>AutoFocus
E. Device>Setup> Management> Logging and Reporting Settings
Answer: B
PCNSE7 dumps full version (PDF&VCE): https://www.lead2pass.com/pcnse7.html
Large amount of free PCNSE7 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDc3F3eHZRclVhZ3c